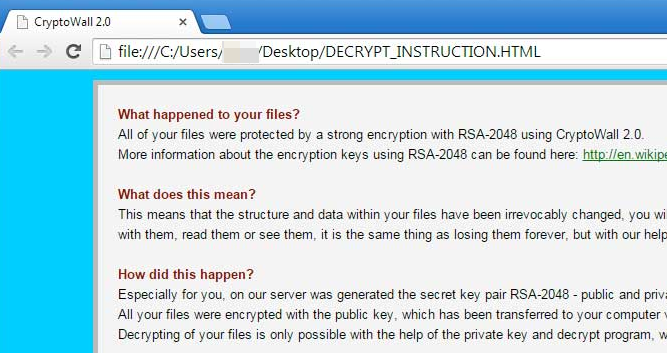
How does the CryptoWall 2.0 virus work? Well, once installed, it starts to encrypt your files in the background and sadly most people do not realize this ransomware virus is on their computer until it displays the ransom note and your files have already been encrypted. The ransom note is a simple HTML file with instructions on how to pay the ransom and get your encryption key. It's not a joke, it's a very serious problem. Here's how the DECRYPT_INSTRUCTION.HTML reads:
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 2.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
And finally, there are instructions on how to pay the ransom and recover your files. Usually, there are a few links to TOR websites, for example tor4pay.com, pay2tor.com, tor2pay.com, and pay4tor.com. As I said, they are all unique for each victim ending with personal identification numbers.
CryptoWall 2.0 uses the RSA-2048 encryption algorithm to encrypt your files. Once your files are encrypted, it deletes the original files and if you don't have back ups there's really not much you can do to get them back.
Many of us spend a significantly high proportion of our time on a computer and on the Internet. And that leaves us open to attack by any number of viruses and different types of malware. And one of the most unpleasant of all of these is something called ransomware. This nasty Internet menace can cause untold harm to both your personal, and your PC's, security.
Despite what many people think, and despite its malicious characteristics, CryptoWall 2.0 is not actually a virus. But whatever you decide to call it, one thing is certain and that is that you really don't want it installed on your computer! They say that to be forewarned is to be forearmed, so let's take a closer look at what ransomware is, what effect it can have, and how to avoid it.
It's main 'modus operandi' is to attack and destroy your files and documents from within your operating system and encrypt personal files that are valuable to you. Such viruses are sneaky and stealthy and will install themselves on your computer by pretending to be something that they're really not - i.e. something harmless and useful. They are also distributed via infected websites and fake emails. How ironic is that?
Unlike a regular computer virus, CryptoWall 2.0 doesn't replicate itself and infect other PCs and users. What it will do however is encrypt your files and install more malware on your computer. Which in turn creates further problems and leaves your online security wide open and defenseless.
Therefore, protecting yourself from this infection is paramount but luckily there are a number of steps you can take to boost your line of defense. First of all, make sure that your PC has a firewall installed and turned on. Also, check that your anti-virus software is a reputable make and is running on the latest version and has up-to-date patches installed. You also need to run it regularly, manually, not just sit back and let it tick away in the background. Finally, don't download programs from untrustworthy sources or third party websites. Stay safe – stay ransomware free.
So what should you do your files have been encrypted? Easy to say, but try not to panic and most definitely do not pay any money unless the encrypted files are very important and you can't afford to lose them. If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer and specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that scammers will recover your files.
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing CryptoWall 2.0 and related malware:
Before restoring your files from shadow copies, make sure CryptoWall 2.0 is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by CryptoWall 2.0 virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Before using Shadow Explorer, you can try to decrypt some of your files using RakhniDecryptor.exe and RectorDecryptor.exe from Kaspersky. These tools might help you, but please note that they were not designed decrypt the data encrypted by this ransomware virus. However, you can still try them.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
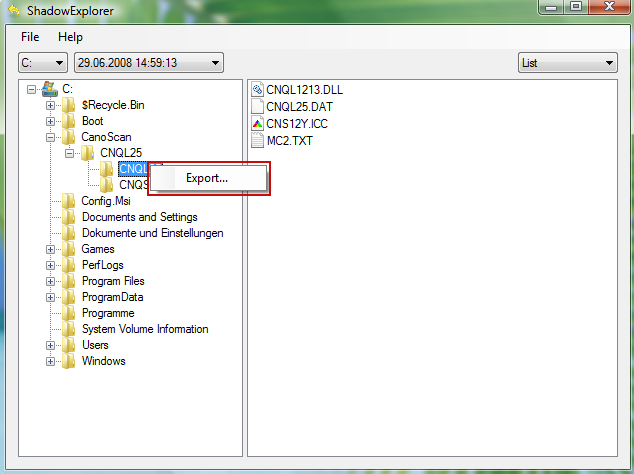
Hopefully, this will help you to restore all encrypted files or at least some of them.





0 commentaires:
Enregistrer un commentaire